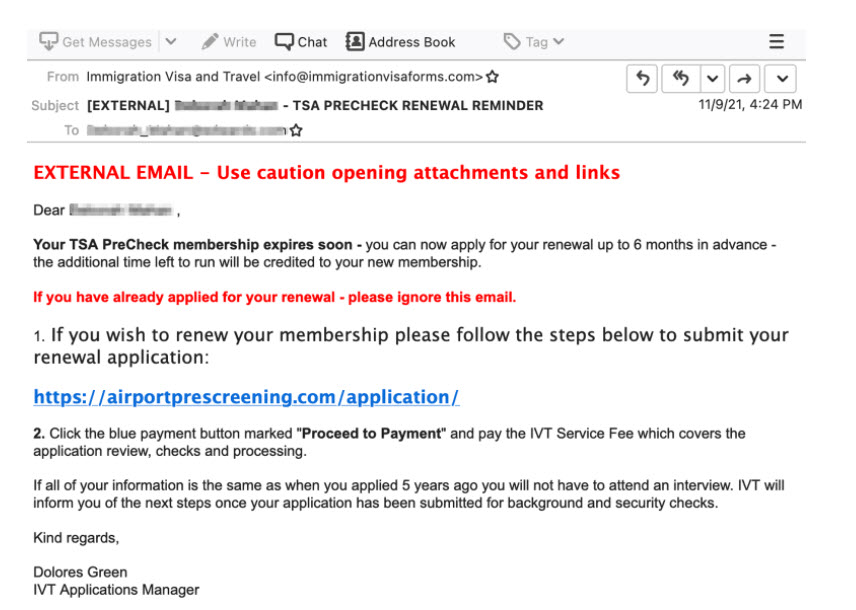
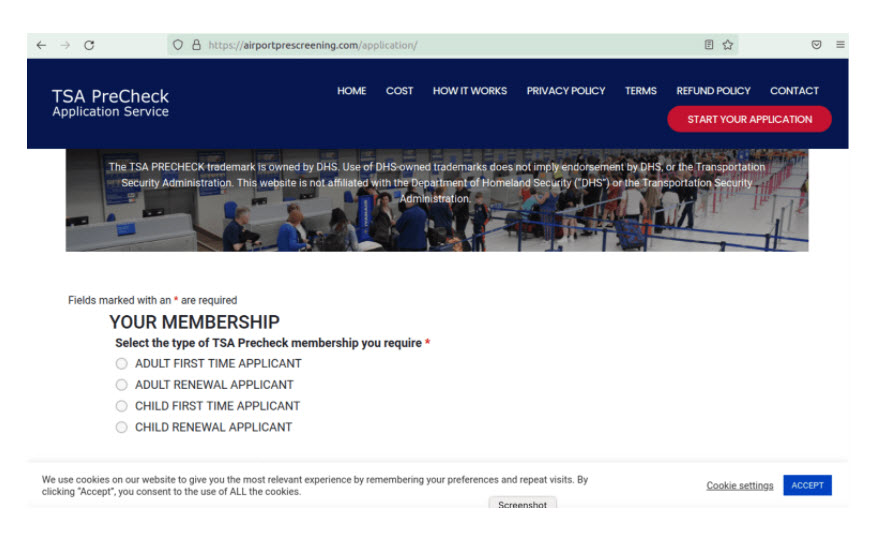
There are resurging scams targeting bank customers that we want to bring to your attention. The scams were initiated differently; however, their ultimate goal was the same – to get to your hard-earned money. In one instance, the customer received a text message stating that their Apple ID had been compromised and that the customer needed to call the number provided in the text to resolve the issue. In a different case, the customer’s computer screen displayed a black screen with a message from “Microsoft” prompting the customer to call the number provided on the screen in order to repair their computer.
When the customer calls the number, the scammer informs them that their bank account had been compromised and they are asked to provide their debit card number along with other identifying information. After obtaining the information, the customer is transferred to the bank’s supposed fraud department where a different scammer informs them that their money is not safe due to a compromise by bank staff. The customer is advised to immediately withdraw their money. The scammers actually stay on the phone while the customer conducts the withdrawal and then direct them to deposit the cash at a specific bitcoin ATM in order to “keep it safe”.
Please keep the following red flags of common tech support/cryptocurrency scams in mind to avoid being the next victim:
- You receive an unsolicited phone call, text message, email, or a pop-up prompt noting that your computer is compromised.
- You are asked to call an unknown number, or are automatically transferred, for further support.
- You are asked to provide additional information about yourself.
- You are asked to provide access to your computer or for you to perform certain actions on your device, such as downloading software or going to a specific website.
- You are instructed not to disclose to bank personnel the reason for the cash withdrawal.
- They shift the conversation from the initial topic (e.g. device issue to compromised bank account).
- You are asked to withdraw a large sum of money and deposit it into a different account not owned by you (e.g. bitcoin ATM) in order to keep the money safe.
- You are asked to pay in cryptocurrency for services. No legitimate business is going to demand that you send your payment in cryptocurrency.
Remember to only use known contact information when calling the bank or any other business. If you are uncertain of the legitimacy of the call, immediately hang up and call the bank using a verified contact number. Never call or respond to a number that was initially provided. In addition, be cautious of depositing your money into cryptocurrency ATMs.
To learn more about tech support or cryptocurrency scams, visit the Federal Trade Commission Consumer Advice site: https://consumer.ftc.gov/articles/how-spot-avoid-and-report-tech-support-scams or https://consumer.ftc.gov/articles/what-know-about-cryptocurrency-and-scams.
Report fraud to the Federal Trade Commission: https://reportfraud.ftc.gov
As always, River City Bank is here for you. Should you have any questions about your personal or financial information or fear you may be a victim of a financial scam, reach out to our Customer Service Team at (916) 567-2899 or (800) 564-7144 or by email at [email protected].